[ad_1]
Beware of malicious recruiting websites
– Jonathan Zhang, CEO at Whois XML API
Walnut, Calif. – May 4, 2022
With the current global unemployment rate surpassing that recorded during the 2008 financial crisis, millions of people are actively seeking jobs. There is a malicious campaign that takes advantage of individuals looking for employment or career advancement — Operation Dream Job.
The campaign was first seen in 2020 targeting government employees. In February 2022, it was again observed luring hundreds of individuals working for news organizations, software vendors, domain registrars, and web hosting providers.
How wide is the scale of the operation? Domain intelligence tells us that it could span thousands of job-related domains. However, Operation Dream Job shouldn’t be the only thing to worry about. Employment fraud campaigns are also on the rise, with 4,000 scam and phishing emails targeting students sent every day. The actors behind these, too, can weaponize employment-related domains to lure victims.
Domains Potentially Connected to Operation Dream Job and Employment Fraud
The actors behind Operation Dream Job used fake job recruitment domain names, such as disneycareers[.]net, find-dreamjob[.]com, indeedus[.]org, varietyjob[.]com, and ziprecruiters[.]org.
A satellite view of domain intelligence enabled us to discover thousands of similar domains. In particular, we found:
- 15,000+ domains containing generic job-related text strings, such as “career,” “find job,” “dream job,” and “recruit” added between January 1 and April 5, 2022
- 700+ domains using the names of popular job-hunting sites added from January 1 to April 5, 2022
- 1,000+ domains related to cybersecurity careers
You may download a sample of the data related to possibly related domains from our website.
Of course, not all of the domains are malicious. Still, hundreds of them should be treated with suspicion and flagged, if not blocked, by security systems. Below are three types of job-hunting domains everyone should keep an eye on.
Cybersquatting Domains
As a general rule, cybersquatting domains are bad news. They could be registered by threat actors planning to use them in malicious activities like phishing, fraud, misinformation, and spam campaigns.
The job-hunting sites the domains in the study imitated include LinkedIn, Indeed, Glassdoor, and Zip Recruiter. Examples of the cybersquatting domains we found are:
- financemanagerglassdoor[.]com
- glassdoor[.]com[.]pl
- glassdooruk[.]com
- indeed-bio[.]com
- indeeduae[.]com
- indeedjobs[.]online
- secretlinkedin[.]ca
- linkedin2[.]tech
- linkedini[.]com
- ziprecruiters[.]org
- ziprecruiter[.]vegas
- zipperrecruiter[.]com
Operation Dream Job also used similar cybersquatting domains like indeedus[.]org and ziprecruiters[.]org.
Domains Hosting Look-Alike Content
While cybersquatting domains imitate popular entities, they may remain benign unless activated and used in malicious campaigns. It becomes worrisome when these domains start hosting questionable content, especially those that look very similar to that seen on the impersonated entities’ sites.
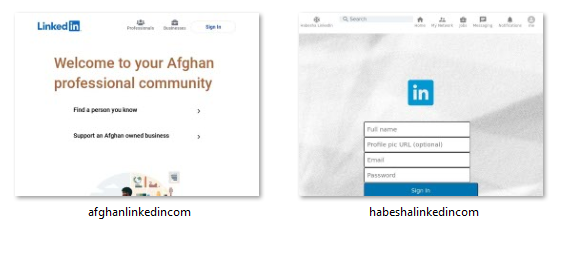
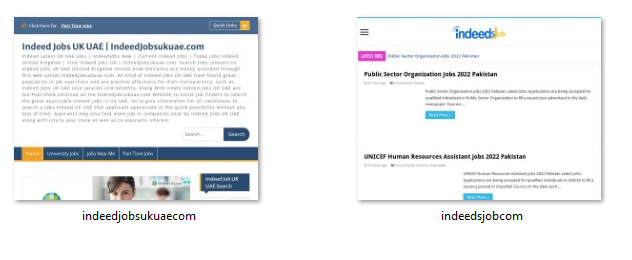
Our screenshot analysis revealed suspicious content, including those that imitated Linkedin’s login page. Below are a few examples.
Website screenshots of afghan-linkedin[.]com and habeshalinkedin[.]com
Website screenshots of indeedjobsukuae[.]com and indeedsjob[.]com
Malicious Job-Hunting Domains
Naturally, we want to be on the lookout for malicious domains. Dozens of the job-hunting domains were flagged by various malware engines. Some examples are:
- masterrecruitment[.]live
- pinchhitterjapanrecruit[.]com
- theboutiquerecruiter[.]com
- recruiting-hamburg[.]com
- moderators-recruitment[.]com
- careersatvalentic[.]com
- lmcocareer[.]org
- stoodcareer[.]com
- goprocareer[.]com
As you can see, these are not cybersquatting domains. As such, it’s not enough to only watch out for look-alike domains.
Cybersecurity-Related Job-Hunting Domains
When we zoomed in on the cybersecurity job market, we found over a thousand related domains that combine “career” and “job” with text strings like “cybersecurity,” “ciso,” “cio,” and “pen test.”
Examples include cybersecurity[.]career, cybersecurityjob[.]ru, cisojob[.]ml, cio[.]jobs, ciojobs[.]xyz, cioscareershub[.]com, pentest[.]careers, and jobsinpentesting[.]net. Several domains seem to impersonate AccioJob (acciojob[.]com), a tech employment placement platform based in India.
A few domains, including cybersecurityjobs[.]tech, have already been flagged as malicious.
When the unemployment rate is high, people exhaust every available resource to find jobs. Tough times, indeed, call for tough measures. Unfortunately, threat actors know that and may exploit the victims’ eagerness.
WhoisXML API’s WHOIS and DNS intelligence can uncover and attribute suspicious domains related to NFT and other mechanisms favored by scammers. Contact us for more information.
– Jonathan Zhang is the founder and CEO of WhoisXML API—a domain and IP data intelligence provider that empowers all types of cybersecurity enterprises to build better products and achieve greater network security with the most comprehensive domain, IP, DNS, and cyber threat intelligence feeds. WhoisXML API also offers a variety of APIs, tools, and capabilities, including Threat Intelligence Platform (TIP) and Domain Research Suite (DRS).

Precise and exhaustive data is vital for cyber-security professionals to analyze and prevent cyber crime. Whois XML API offers a comprehensive collection of domain, WHOIS, DNS and threat intelligence data feeds that are essential to their work. It’s an exhaustive Cyber-security package that offers a maximum coverage of both real-time and historic data, complete with instruments for threat hunting, threat defense, cyber forensic analysis, fraud detection, brand protection, data intelligence enrichment across variety of SIEM, Orchestration, Automation and Threat Intelligence Platforms.
The post Operation Dream Job Is A Nightmare appeared first on Cybercrime Magazine.
[ad_2]
Source link